This incident can be given the name of sophisticated cyber attacks. Hackers’ latest escapades entail cyberattacks on more than 130 organizations where they managed to steal approximately 9931 login credentials, compromising the corporate system, IT sectors in the States and their networks. The group IB report states that the “oktapus” phishing kit was the weapon used to lure victims and target forms into being vulnerable and giving up their credentials.
The attempted cyber attack on Twilo, Doordash & Cloudflare earlier in August has left them shaken and wary. This gang started out with the Okta customers, sending them malicious links at the pretence of the company harvesting all the work login credentials and multifactor authentication codes, giving them full access. This is how they have acquired the nickname of ‘Oktapus’ from the analysts of Group IB.
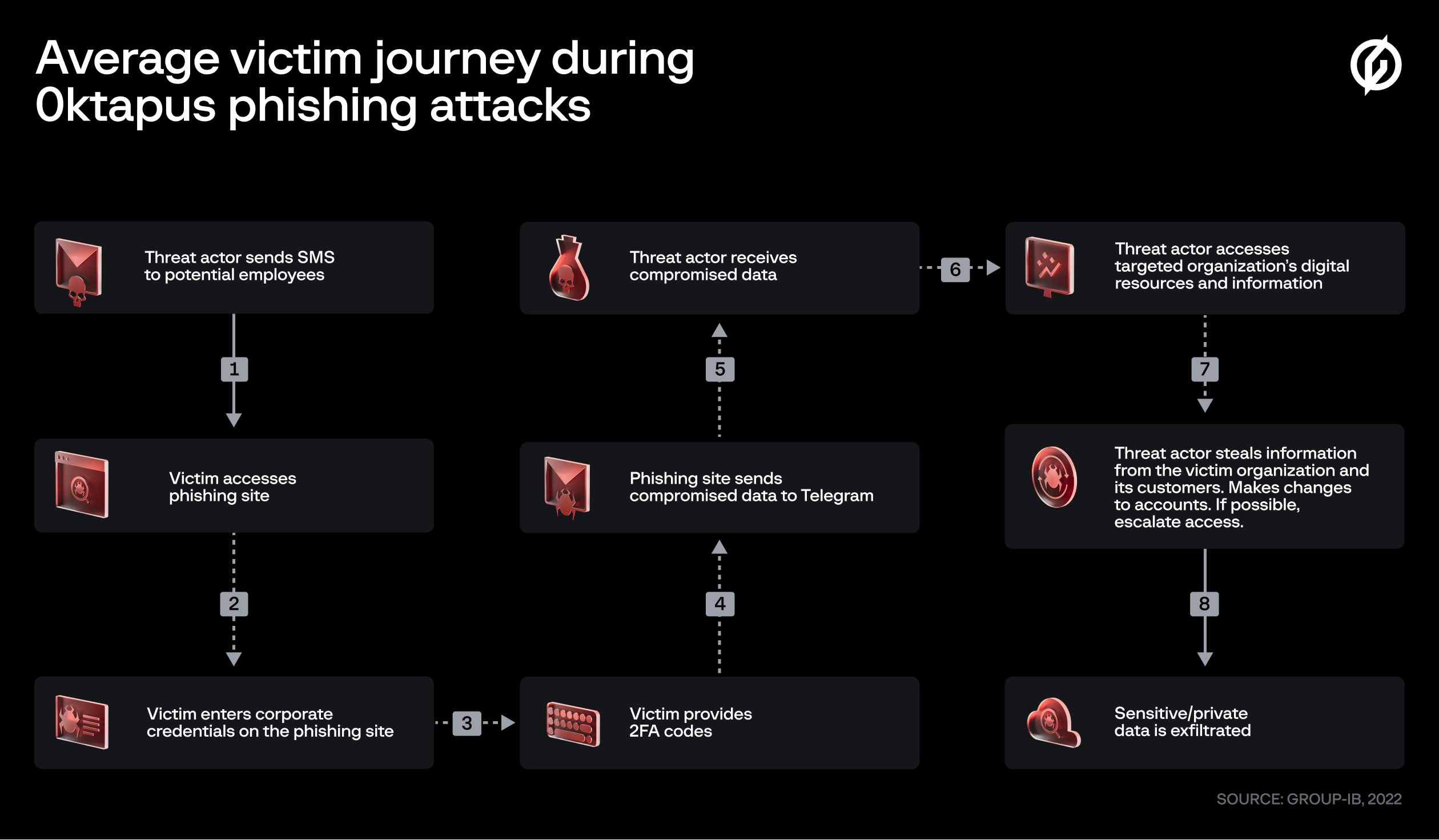
Group IB researchers came forth & informed that “the initial objective of the attackers was clear – obtaining Okta identity credentials and 2FA codes from the users of the targeted organizations” – Roberto Martinez and Rustam Mirkasymov.
This information enabled the hackers to gain unauthorized access to enterprise resources which are meant for the victims.
These authorisation codes were used to perform several supply chain attacks. Klaviyo’s marketing firm was broken into, and so was Mailchimp’s email service from where they reaped DigitalOcean’s consumer email IDs.

The hackers tried to attack Cloudflare but fortunately didn’t succeed in this nefarious task, but unfortunately, Twilo were not so lucky. Infiltration inside Twilo allowed them access to Twilo customers’ signals, from where they gained customer phone IDs and registration codes for approximate 1,900 users. All in all, the technocrats accumulated 169 domains involving Oktapus.
This phishing site was almost identical to the original website, which made asking users & employees for their user ID and 2FA codes all the easier. These stolen credentials were trafficked to a cyber-controlled Telegram network where the miscreants used them to access internal documents, emails and sensitive information from corporate firms.

The attacked companies can be broadly categorized into – 52 software companies, 22 in telecommunication, & 21 business service providers. It was also said that ‘Furthermore, some of the targeted companies provide access to crypto and assets and markets, whereas others develop investment tools.’
Everything is still under investigation & the public probably wouldn’t know of it all until much later. Even though it has been exposed,, hackers got full access to 93 accounts and all of them have been thoroughly checked. The users and the rest have been cautioned about any weird behaviour or suspicious activities.
For more such updates, keep reading techinnews



